An investigation conducted by the Vulnerability Research Group and Malware, Check Point, revealed that the Microsoft Help Files They are being used by cybercriminals for distributing malicious code. In addition, the security expert highlighted the fact (fact) the vast majority of antivirus programs are unable to detect malware hidden in these files.
According to Oded Vanunu, responsible for Check Point Research Group, “The CHM files are usually used as documentary software and how tutorial help. Since its use is very common, it is also unlikely that users suspect this online help. “
Microsoft Compiled HTML Help is a proprietary Help format consisting of a collection of pages HTML, as well as a series of indexing and browsing tools. These files are compressed and installed a binary format with the extension CHM (Compiled HTML). The researchers found that CHM files can be used to execute malicious code on a computer that works with Microsoft Windows Vista or higher.
According to research, when a user starts an infected Microsoft Help file, starts an application for discharge and execution of the piece of malware. The captured samples, the malicious payload had the name PuTTY , a popular network client that supports SSH and Telnet protocols, and allow remote connections. That is, cybercriminals are to mask the malware, making him pass as unnoticed as possible.
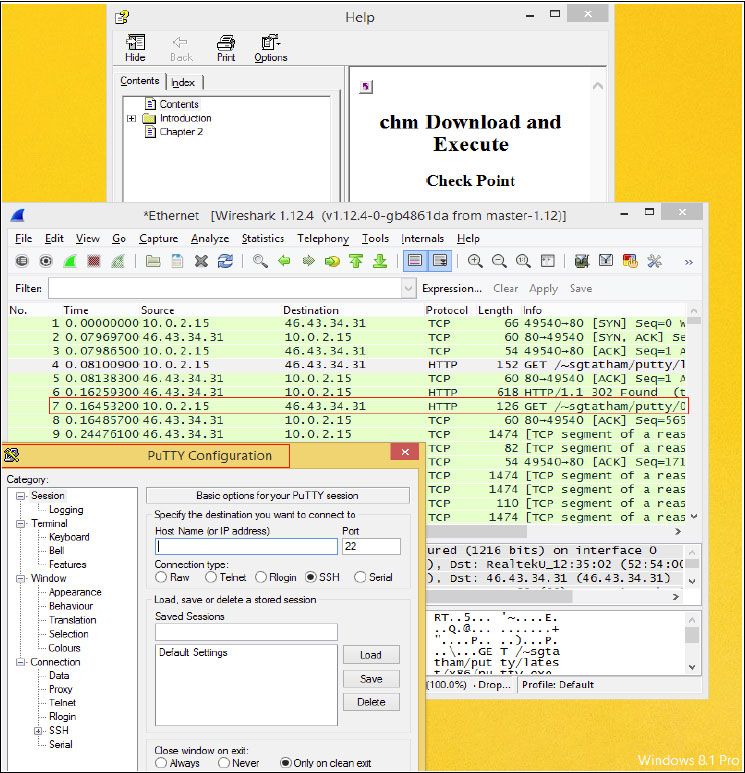
“After analyzing a sample of the malware, we found that the load useful was only seen by a small number of antivirus (3 in 35), “said Vanunu. However, the most worrying is that the researchers also found that it was possible to handle the load to make it completely invisible to security products, which makes it a highly dangerous method.
Check Point’s Research Group found that cybercriminals who are behind this technique use to the spread of malware, attack campaigns through social networks and spam. Attackers can prepare credible messages that promote versions or well-known programs and whose documentary files are compromised.
“As a test, we were able to eliminate the malware URL directly sample and replace it for a harmless discharge of putty.exe program. With some additional modifications, we got a sample with a zero detection rate by updated antivirus products. This case is just another example of how cybercriminals use a variety of techniques to achieve evade the radar of antivirus detection, “ concludes Vanunu.
Researchers from Check Point announced a few days ago through a post on his blog this route of infection
.
No comments:
Post a Comment